Highlights
- Hackers target WordPress admin emails for attacks like phishing, brute force, and account takeovers.
- Outdated or vulnerable plugins and themes can expose admin emails to hackers.
- SQL injection
- is a common method used by hackers to extract admin emails from WordPress databases.
- Publicly displayed emails and social engineering tactics make admin emails vulnerable to exploitation.
- Strong passwords, two-factor authentication, and regular updates are essential for securing WordPress admin emails.
As the most popular content management system (CMS) worldwide, WordPress powers over 40% of all websites on the internet. Given its widespread use, hackers seeking to take advantage of weaknesses will inevitably find it to be a desirable target.
Getting admin email addresses is frequently one of their main objectives, as this can lead to a variety of harmful operations. Once hackers gain access to the admin email, they can launch brute force attacks, phishing attempts, or even password resets to hijack the site.
In this article, we’ll see some of the common methods that hackers use to mine WordPress websites. Also, we will see strategies to protect your website from these threats.
Why Hackers Target Admin Email Addresses
Admin email addresses play a critical role in WordPress site management. They are used for crucial functions like account recovery, receiving site notifications, and making important changes to the site’s configuration.
Hackers target admin emails because gaining access to them can be the first step toward a full-scale security breach. Some of the reasons why hackers want admin email addresses are:
- Account Takeover
With WordPress admin email extraction, hackers can initiate a password reset request, potentially gaining access to the WordPress dashboard. Once inside, they can modify site content, install malicious plugins, or even lock the legitimate owner out of their website.
- Phishing Attacks
Admin emails are often used in phishing campaigns. Hackers can impersonate legitimate sources and send fake emails to admins, tricking them into revealing their credentials or clicking on malicious links.
- Further Exploitation
The admin email can be used to uncover other vulnerabilities in the website, or it may be linked to other platforms, giving hackers a broader attack surface.
Given these risks, it’s essential to understand the methods hackers use to extract admin email addresses and how to prevent such attacks.
5 Common Techniques Hackers Use to Mine WordPress for Admin Email Addresses
1. Brute Force Attacks
Brute force attacks involve hackers trying multiple combinations of usernames and passwords until they gain access to the admin dashboard. Once they break in, the admin email is readily accessible from the settings.
How to Protect Against Brute Force Attacks
- Use complex passwords that include a combination of letters, numbers, and symbols.
- Limit the number of login attempts with plugins like “Limit Login Attempts Reloaded.”
- Enable two-factor authentication (2FA) to add an extra layer of security, requiring more than just a password to log in.
2. Exploiting Vulnerable Plugins and Themes
WordPress’s rich ecosystem of plugins and themes allows site owners to customize their websites. However, not all plugins and themes are secure. Hackers often adopt tactics for WordPress vulnerability exploitation to gain unauthorized access to sites, including the admin email address.
Outdated Plugins and Themes
When plugins and themes are not regularly updated, they can contain known vulnerabilities that hackers can exploit. For instance, a security flaw in a popular plugin may allow attackers to execute malicious code on the server.
Backdoors in Plugins
Some poorly maintained or malicious plugins may contain backdoors, giving hackers continuous access to the site even after the initial vulnerability is patched. Once in, they can extract sensitive data, including admin email addresses.
How to Protect Against Plugin and Theme Exploits
- Regularly update all plugins and themes to their latest versions.
- Use trusted, well-reviewed plugins from the official WordPress repository or reputable developers.
- Remove any unused or outdated plugins and themes to reduce the risk of exploitation.
3. SQL Injection Attacks
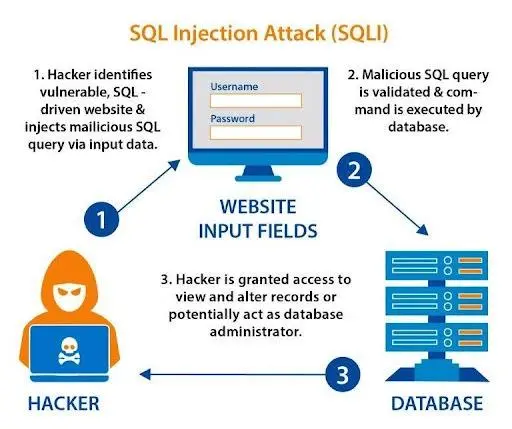
SQL injection is a common attack method where hackers manipulate SQL queries to gain unauthorized access to a database. If a WordPress site has vulnerabilities in its code, a hacker can extract sensitive information, including admin emails, directly from the database.
Malicious SQL Queries
Hackers may insert malicious SQL code into form fields or URLs, enabling them to extract data from the database. This can include sensitive data like user credentials and admin email addresses stored in the `wp_users` table.
How to Protect Against SQL Injection
- Use security plugins like Wordfence or Sucuri, which can block malicious requests.
- Always sanitize and validate user inputs to prevent SQL injection vulnerabilities.
- Regularly update your WordPress core files, plugins, and themes, as updates often include patches for known vulnerabilities.
4. Scraping Public Information
Many WordPress sites inadvertently expose admin emails through publicly accessible content. Hackers use automated bots to scrape websites for such information, which they can later exploit.
Web Scrapers
Hackers use crawlers to scan websites and collect email addresses that are displayed on contact pages, user profiles, or blog posts. This can lead to further attacks, such as phishing or brute-force login attempts.
Public Contact Forms
Some websites unintentionally expose admin email addresses in their contact forms or email headers. If these forms aren’t properly secured, hackers can extract the email address.
How to Protect Against Scraping
- Avoid displaying your admin email on publicly accessible pages. Use a separate email address for public contact forms.
- Use an email obfuscation plugin to hide your email address from bots.
- Implement CAPTCHAs on your contact forms to prevent bots from submitting malicious requests.
5. Social Engineering and Phishing
Social engineering attacks rely on manipulating individuals into divulging sensitive information. Hackers may impersonate trustworthy entities, such as technical support staff or other administrators, to trick you into revealing your admin email or other credentials.
Phishing Emails
Hackers can send fake emails that appear to come from legitimate sources, asking the admin to verify account details or click on a malicious link. These emails may include links to phishing sites designed to capture login credentials.
Impersonation
- By impersonating a trusted entity or using publicly available information (like social media profiles), hackers can persuade admins to share their email or other sensitive information.
- How to Protect Against Social Engineering Attacks
- Be cautious of unsolicited emails asking for account information or password resets.
- Verify the authenticity of requests before sharing sensitive information. When in doubt, contact the source directly through official channels.
- Use spam filters and phishing protection plugins to block fraudulent emails.
Other techniques
Automated Tools
Hackers often use tools like WPScan or Hydra to automate the process of trying thousands of login combinations. These tools can quickly test numerous username-password pairs, increasing the chances of a successful breach.
Weak Passwords
Weak or common passwords are particularly vulnerable to brute-force attacks. Admins using simple passwords (like “admin123”) are easy targets, making it crucial to use strong, unique passwords for all accounts.
How to Secure Your WordPress Admin Email
Now that you understand ways of Hackers targeting WordPress admin, it’s crucial to implement the following best practices to safeguard your site:
Use a Unique Admin Email Address
Avoid using generic email addresses like `admin@example.com` that are easy for hackers to guess. Create a unique and private email address for your WordPress admin account that isn’t publicly visible on your site.
- Enable Two-Factor Authentication (2FA)
Two-factor authentication adds a layer of security, requiring not just a password but also a secondary form of verification (e.g., a code sent to your phone). Even if a hacker gains access to your admin email, 2FA will prevent unauthorized logins.
- Regular Security Audits
Regularly scan your site for vulnerabilities using tools like Wordfence, Sucuri, or MalCare. These tools can help identify security flaws, such as outdated plugins or unauthorized login attempts, and protect your site against breaches.
- Keep Plugins, Themes, and WordPress Core Updated
Always ensure that your WordPress installation, along with all plugins and themes, is up to date. Developers frequently release updates to patch security vulnerabilities.
- Limit Login Attempts and Use Strong Passwords
Install a plugin that limits the number of failed login attempts. Combine this with strong, unique passwords to reduce the risk of brute-force attacks.
Conclusion
We hope you got your answer on how do hackers mine WordPress for admin email addresses. Hackers employ a variety of techniques to mine WordPress for admin email addresses, ranging from brute force attacks and SQL injections to exploiting vulnerable plugins and themes. Once they obtain the admin email, it opens the door to a host of malicious activities, such as phishing attacks, spam distribution, and account takeovers. However, with our WordPress development services, you can rest assured about your website security. So, feel free to contact Tambena Consulting for any queries regarding your WordPress website development and its security.






